
Table of Contents
Top 7 API Security Threats in 2025 You Can’t Miss
APIs have become the invisible engine behind every app you use—from online shopping to digital banking. But while they make life easier for users and developers alike, they have also opened the door to a new generation of cyber threats.
In 2025, APIs aren’t just a convenience—they’re the most targeted part of your application stack. This blog will explain the top 7 API security threats—and how your business can stay ahead of attackers.
What are APIs, and why do we have them?
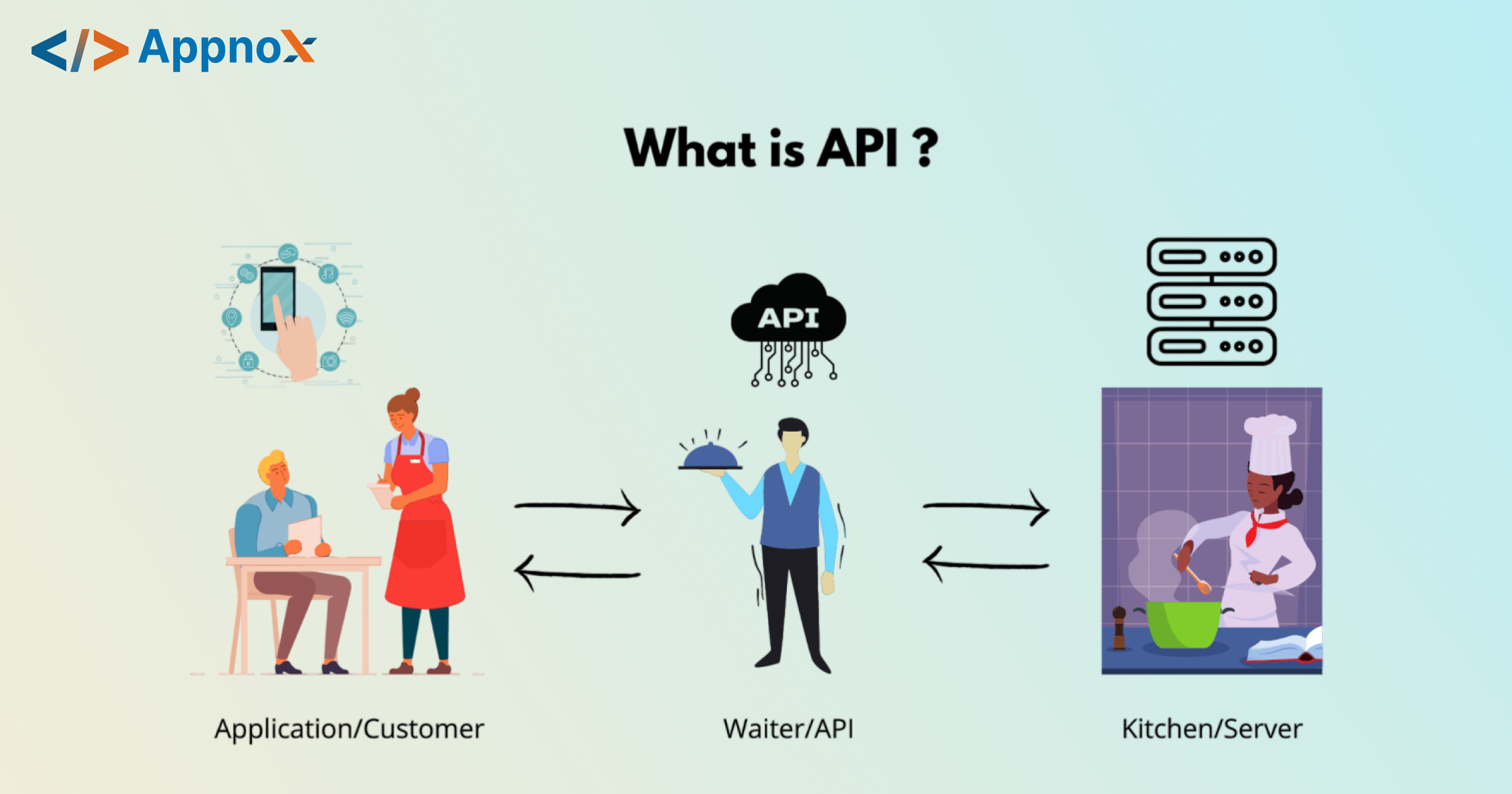
Picture an API (Application Programming Interface) as a computerized waiter. As a waiter takes your order and brings food from the kitchen, an API enables apps to communicate with servers to get data — you want to book a flight or refresh your profile.
In technical terms, APIs are the bridges that let software systems interact. When you book a flight and hotel through one app, APIs are behind the scenes connecting airlines, payment systems, and hotels in real time.
Example: When you use a travel app to book a flight and a room together, that app is using APIs to communicate with multiple services on the fly.
Today, APIs drive 83% of all web traffic. You’ll find APIs in everything from banking apps and e-commerce checkouts to social media and healthcare platforms.
But there’s a catch:
The greater the number of APIs you utilize, the more doors you open to potential attackers.
Why API security matters now more than ever.
Attackers have shifted focus. Rather than hitting the web directly, they are looking for APIs. ”Why?
Because:
- These APIs are usually not documented (a.k.a. “shadow APIs”).
- APIs aren’t monitored by traditional security tools.
- Developers accidentally leak sensitive data all the time.
The Core elements of API Security :
- At least one API incident occurred at 74 percent of companies over the past year. (Salt Security, 2025)
- 94% of APIs are undocumented or dark API Security. (Gartner)
- 62% of attacks are not discovered for weeks due to insufficient real-time visibility on the part of most teams. (Gartner/CyCognito)
Most companies do not even know how many of their APIs are publicly exposed, unsecured, and undocumented. This is a serious issue with a high potential for data exfiltration or system takeover. Enter Appnox Technologies, a company whose vision I like. Businesses need modern protection, and this is where solutions like Appnox Technologies come into play.
The Top 7 API Security Threats in 2025 (and How to Fix Them)
Let’s break them down simply, so anyone can understand.
1.Broken Object Level Authorization (BOLA)
What it is ?
Hackers manipulate something in the URL to get to someone else’s private data.
Why is it dangerous ?
It is one of the most popular API vulnerabilities and can expose user accounts, order info, or even admin controls.
How to prevent it ? :
- Add object-level authorization at the back end.
- Use non-guessable, encrypted IDs.
- Record and track all requests to access objects.
2.Excessive Data Exposure
What it is ?
The response from the API sends too much data, even if it doesn’t all get displayed on screen.
Why is it dangerous ?
If you look at the API response, hackers are able to readily pull personal data (emails, phone numbers, internal system info) from it.
How to prevent it ? :
- Only return the fields that the user asks for.
- Never rely on the front end to hide security-endemic information.
- On the back end, use role-based filtering.
3.Security Misconfiguration
What it is ?
When deployed, APIs are exposed with weak settings, such as leaving debug mode enabled or leaving detailed error messages on.
Why is it dangerous ?
Misconfigurations are difficult to find, but attackers can use them to figure out how to break in.
How to prevent it ? :
- Leverage secure-by-default settings.
- Exclude stack traces and server information from error messages.
- Perform periodic configuration assessments.
4.Lack of rate limiting
What it is ?
APIs are unlimited and open to brute force and scraping.
Why is it dangerous ?
Attackers can cause your system to crash or steal gigabytes of data, all without tipping you off.
How to prevent it ? :
- Limit requests by users or IP addresses.
- Adopt a CAPTCHA or token-driven authentication process.
- Use with anomaly detection software.
5.Mass Assignment
What it is ?
APIs also enable users to submit additional fields, and these additional fields can override protected data (such as changing someone else’s password).
Why is it dangerous ?
Hackers can guess field names and tamper with values they shouldn’t influence.
How to prevent it ? :
- Define allowed input fields explicitly.
- “Use input validation and schema enforcement.”
- Sanitize all incoming data.
6.Injection Attacks
What it is ?
When injecting malicious code into API inputs, hackers can dupe the server into executing dangerous commands.
Why is it dangerous ?
It can reveal an entire database, leak credentials, or crash systems.
How to prevent it ? :
- Use parameterized queries.
- Perform input validation and input sanitization.
- Don’t ever call dynamic SQL from any user input.
Improper Asset Management
What it is ?
Historical, unused, or undocumented APIs can be found on the web.
Why is it dangerous ?
These “forgotten” APIs are low-hanging fruit; nobody is keeping an eye on them.
How to prevent it ? :
- Keep your API inventory up to date.
- Monitor and log all test/dev versions of endpoints.
- Concisely retire dead APIs.
Final Thoughts: Protecting the New, Modern Ways
Traditional firewalls and legacy systems are by no means sufficient on their own to keep APIs safe. As threats evolve quickly, businesses require proactive, real-time services.
Appnox Technologies is an API-first security company with:
- Zero-day threat detection
- Real-time visibility
- No code changes are required.
Is your API truly secure? Let Appnox tell you how you can find that out. Discover more about our products: appnox.ai . Explore our solutions at appnox.ai.
FAQ’s
Q1: What threat has caused the increase in attacks on APIs?
APIs are designed for being open and flexible, and with that, the door to potential breaches is open too. But many are not registered or so poorly secured that conventional tools may have a hard time monitoring their behavior.
Q2: Do traditional firewalls protect APIs?
A: Not effectively. Firewalls were built to secure networks, not APIs. APIs require specialized monitoring and behavioral analysis. That’s why solutions like Appnox offer API-specific protections with zero-day threat detection and real-time analytics.
Q3: How can I check whether my APIs are susceptible to this?
A: If you do not know where all of your APIs are — or if they are exposed to the public, if they are not up to date — you are taking chances. Services like Appnox offer immediate API discovery, visibility, and security posture insight to reduce risks before they occur.
Found this post insightful? Don’t forget to share it with your network!
Read More Guides

IoT Security Essentials: How Devices Get Hacked (and How to Stop It)

Top AI Trends Transforming Business in 2025




